Malware is spread through phishing, so we must remember the importance of not installing apps from suspicious links.
Generated decorative illustration
Banking malware is one of the most dangerous types of malware out there, as it allows users to gain access to a victim’s bank account. Over the past few months, we’ve talked about some of the most high-profile examples, such as a Trojan that restores a user’s phone after emptying their bank account , or Medusa, a banking Trojan hidden in the form of fraudulent apps .

In mid-September, cybersecurity firm Cleafy announced the discovery of a new variant of a banking Trojan known as TrickMo . Following further research by the Zimperium team , this other cybersecurity firm has identified a total of 40 new variants of this same malware in circulation.
Zimperium claims at least 13,000 devices are affected by the malware
The variants analyzed by the Zimperium research team feature the same capabilities that Cleafy mentioned in the original report, from screen recording to remote control of the user’s device, including the ability to intercept two-step verification codes, and more.
New malware discovered on Android that had reached Google Play: there are more than 11 million infected devices
As you might have guessed, TrickMo’s capabilities allow attackers to access all information stored on the device, as well as gain unauthorized access to the victim’s bank accounts. However, there is a new threat that should be kept in mind.
As we have been able to read in the report published by Zimperium, the new version of TrickMo is also capable of stealing the lock code of the users’ mobile, since it has a screen that perfectly imitates the interface from which we enter the code of the device every time we want to unlock it.
TrickMo Fraud Lock Screen Screenshots
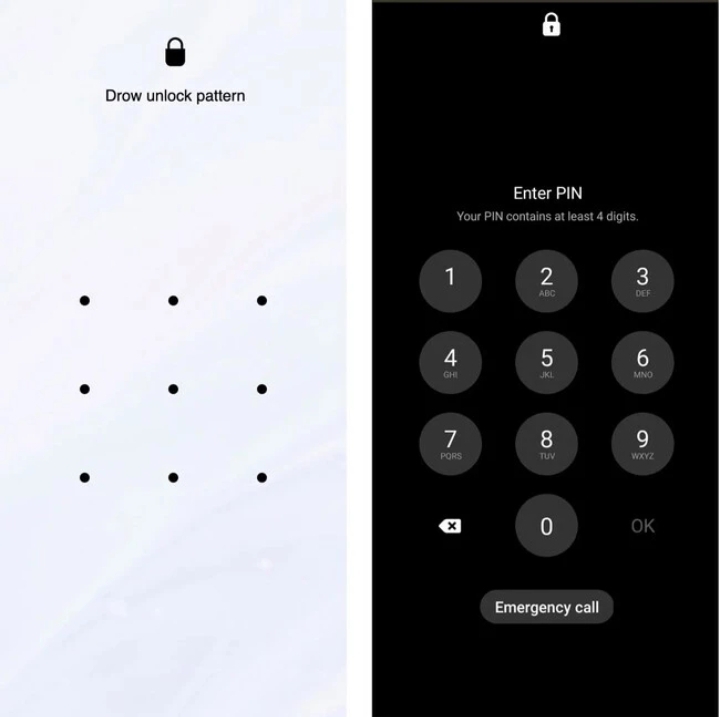
The lock screen is actually a full-screen web page, masquerading as the operating system’s native interface. When the user enters their PIN or unlock pattern, the information is sent directly to attackers , who can then use the PIN to unlock the device when it is not in use.
Zimperium’s team of researchers has gained access to several of the servers used to control the malware, allowing them to find out that there are at least 13,000 affected devices worldwide . The majority are located in Canada, although the number of cases is also significantly high in Germany, the United Arab Emirates and Turkey.
The company claims that attackers gain access to the device through phishing campaigns . With this in mind, it is important to remember the importance of avoiding installing unknown applications through APK files, especially if we have received a link via SMS or email.

